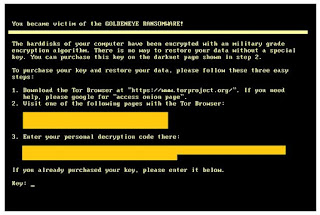
Researchers from MacAfee came across a series of rogue apps on Google store posing as Wannacry protectors. Wannacry is a Ransomware which affects Windows operating system only. But, cybercriminals are taking advantage of the trending topic to trick Android users into installing fake Wannacry protectors on their devices.
These applications are loaded with ads and once installed, they advertise sponsored applications, encouraging users into installing them. These sponsored applications may contain other malware. We advise our readers to follow the tips provided by MacAfee before installing any application:
Be careful what you download
Don’t download anything for WannaCry protection unless it’s from a trusted security provider. More importantly, if the issue does not affect your type of operating system, don’t download anything you don’t need to.
Read app reviews.
Before you even download an app, make sure you head to the review section of an app store first. Take the time to read the reviews, and keep an eye out for ones that mention that the app is falsely advertised, or has had issues with security. When in doubt, avoid any app that seems remotely fishy.
Use a comprehensive security solution.
Whether the newest cyberattack is after your computer or your mobile devices, make sure you cover all of them with a comprehensive security solution.
Source:[
McAfee]