The anatomy of an Anonymous attack
After observing an attack launched by Anonymous last year, security experts from Imperva managed to perform an in-depth analysis of the incident. The results of the analysis are included in a report called The Anatomy of an Anonymous Attack.
The experts analyzed traffic logs, social media communications on the days prior to attack, and identified trends and patterns that characterize these operations.
They don’t name the organization that was targeted, but according to the New York Times, the target was none other than the Vatican, the hacktivists wanting to disrupt an event that occurred at the time.
The attacks performed by Anonymous in 2011 were split into two main categories: reactive attacks, in which the hacktivists target an organization as a form of revenge against its actions, and proactive, in which the hackers announce their intentions to go after an organization.
The latter category of attacks is not as common as the first, this being the category in which the attack against the Vatican falls into.
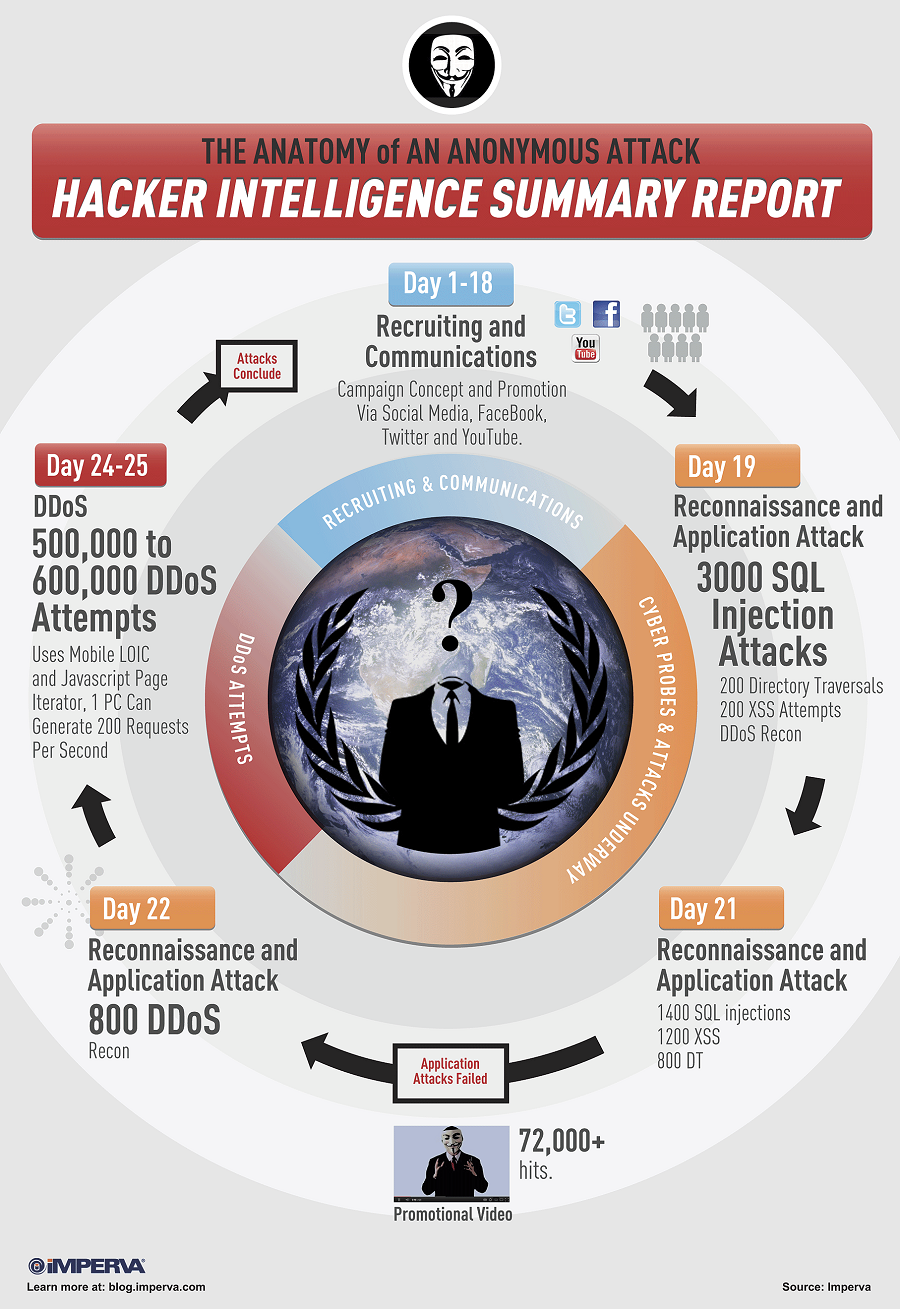
The operation took place over a period of 25 days and it was composed of three main stages. In the first stage, Anonymous promoted its plans using social media channels such as Facebook and Twitter, and recruited supporters for the attack.
In the second phase, around 10 to 15 skilled hackers tested the target in search for security holes that could be exploited in the third stage which represented a distributed denial of service (DDOS) attack.
After analyzing the attack, the security experts concluded that Anonymous hackers rely very much on techniques and technologies utilized by black hats that operate for a profit. The novelty with the hacktivists is the fact that they created websites to help them launch DDOS attacks.
It has been determined by the researchers that Anonymous members usually try to steal data from the site they target, but if they don’t succeed, they turn to DDOS attacks.
The paper also reveals that while there are some skilled hackers, most of them are what they call “laypeople” who are directed by the skilled hackers, their main role being to conduct DDOS attacks. Statistically speaking, in an attack there may be 10 to 15 skilled hackers and a few hundred volunteers.
The main differences between Anonymous and profiteering hackers is that the former seldom use bots and they don’t rely on malware or phishing. On the other hand, the recruiting process takes place in public, unlike with underground black hat teams that recruit their members on hacker forums.
So what can organizations do against Anonymous attacks?
Simply put, “if companies are prepared against application layer attacks and have put in place solid defenses to mitigate SQL injection, cross site scripting, local file inclusion and DDoS, then such enterprises will be well prepped against Anonymous.”
They don’t name the organization that was targeted, but according to the New York Times, the target was none other than the Vatican, the hacktivists wanting to disrupt an event that occurred at the time.
The attacks performed by Anonymous in 2011 were split into two main categories: reactive attacks, in which the hacktivists target an organization as a form of revenge against its actions, and proactive, in which the hackers announce their intentions to go after an organization.
The latter category of attacks is not as common as the first, this being the category in which the attack against the Vatican falls into.
The operation took place over a period of 25 days and it was composed of three main stages. In the first stage, Anonymous promoted its plans using social media channels such as Facebook and Twitter, and recruited supporters for the attack.
In the second phase, around 10 to 15 skilled hackers tested the target in search for security holes that could be exploited in the third stage which represented a distributed denial of service (DDOS) attack.
After analyzing the attack, the security experts concluded that Anonymous hackers rely very much on techniques and technologies utilized by black hats that operate for a profit. The novelty with the hacktivists is the fact that they created websites to help them launch DDOS attacks.
It has been determined by the researchers that Anonymous members usually try to steal data from the site they target, but if they don’t succeed, they turn to DDOS attacks.
The paper also reveals that while there are some skilled hackers, most of them are what they call “laypeople” who are directed by the skilled hackers, their main role being to conduct DDOS attacks. Statistically speaking, in an attack there may be 10 to 15 skilled hackers and a few hundred volunteers.
The main differences between Anonymous and profiteering hackers is that the former seldom use bots and they don’t rely on malware or phishing. On the other hand, the recruiting process takes place in public, unlike with underground black hat teams that recruit their members on hacker forums.
So what can organizations do against Anonymous attacks?
Simply put, “if companies are prepared against application layer attacks and have put in place solid defenses to mitigate SQL injection, cross site scripting, local file inclusion and DDoS, then such enterprises will be well prepped against Anonymous.”
Source: Softpedia