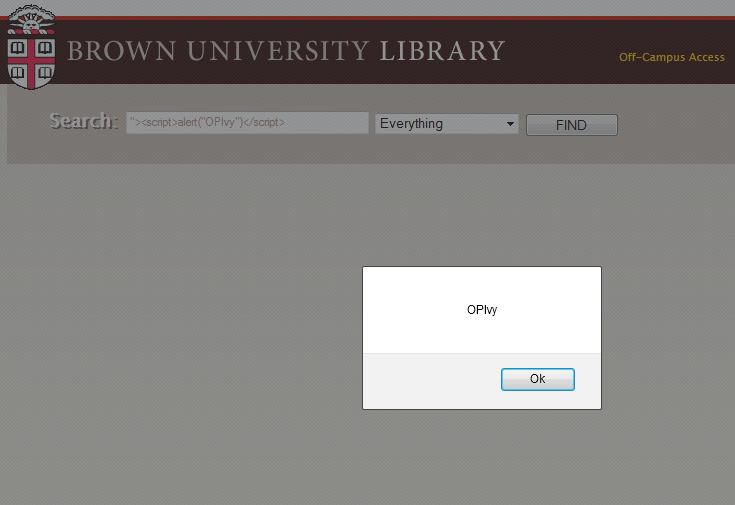
Ivy League Universities Targeted by Hackers in OpIvy
Two grey hat hacker collectives joined forces and launched an operation called Op Ivy, intended to reveal the large number of vulnerabilities present in the official websites of major universities, first ones on the list being Brown University, Columbia University, Dartmouth University, Cornell University, Harvard University, Princeton University, University of Pennsylvania, and Yale University.
TeamHav0k is known for identifying security holes in sites managed by universities, but now they’re being aided by Zer0Lulz in trying to alert webmasters on the flaws and the dangers they pose.
“Two security teams have joined up and have found Cross-Site-Scripting vulnerabilities in the top Colleges in America. It is truly outstanding how these financially stable communities are unable to pay for security,” the hackers wrote in a statement.
“Two security teams have joined up and have found Cross-Site-Scripting vulnerabilities in the top Colleges in America. It is truly outstanding how these financially stable communities are unable to pay for security,” the hackers wrote in a statement.
Each of the university sites listed above contains a cross-site scripting (XSS) vulnerability on one of its webpages, and the hackers provided a list of PoCs to prove their findings.
“As we have said before XSS is a very a very dangerous security breach and vulnerability. Non-persistent, self and persistent are all equally dangerous,” a TeamHav0k spokesman explained.
“As we have said before XSS is a very a very dangerous security breach and vulnerability. Non-persistent, self and persistent are all equally dangerous,” a TeamHav0k spokesman explained.
With their findings Zer0lulz and TeamHav0k hope that corporations and other website owners patch up the XSS flaws that expose their customers to malicious operations.
Here is a complete statement in which the hackers explain the risks presented by these common weaknesses:
They can be used with what is called a ‘XSS Tunnel.’ A XSS Tunnel is where the attacker can then use the victims he/she gets as a botnet and as a SOCKS proxyHypothetically let’s say you were on a XSS Tunnel, the attacker could then link up to you using you as a SOCKS proxy.
From there the attacker can do what he/she pleases but it will appear as if you are doing the actions yourself. Let’s say that while under the SOCKS proxy the attacker hacked into a Government server.
If the attacker were to get caught, it would appear as if the victim executed the attacks. But with XSSF there is a lot more that can be done, the attacker can then open up a backdoor to your computer resulting in a complete OS compromise and do whatever he/she wants.
Here is a complete statement in which the hackers explain the risks presented by these common weaknesses:
They can be used with what is called a ‘XSS Tunnel.’ A XSS Tunnel is where the attacker can then use the victims he/she gets as a botnet and as a SOCKS proxyHypothetically let’s say you were on a XSS Tunnel, the attacker could then link up to you using you as a SOCKS proxy.
From there the attacker can do what he/she pleases but it will appear as if you are doing the actions yourself. Let’s say that while under the SOCKS proxy the attacker hacked into a Government server.
If the attacker were to get caught, it would appear as if the victim executed the attacks. But with XSSF there is a lot more that can be done, the attacker can then open up a backdoor to your computer resulting in a complete OS compromise and do whatever he/she wants.
Source:Softpedia